United suffered a significant data hack at the end of last year. Miles are regularly for sale on the Darknet. So IT security is something that many programs are doing more than paying lip service to.
They’re telling members to change passwords, thinking that they don’t want the password used on their site to be the same as passwords used else in case someone else’s data gets breached. (Good luck with that. Many suggest Lastpass, though if you use Lastpass make sure to change that password as Lastpass was hacked.)
There are some basic best practices, a thought that occurred to me as I read this email a reader forwarded from United.
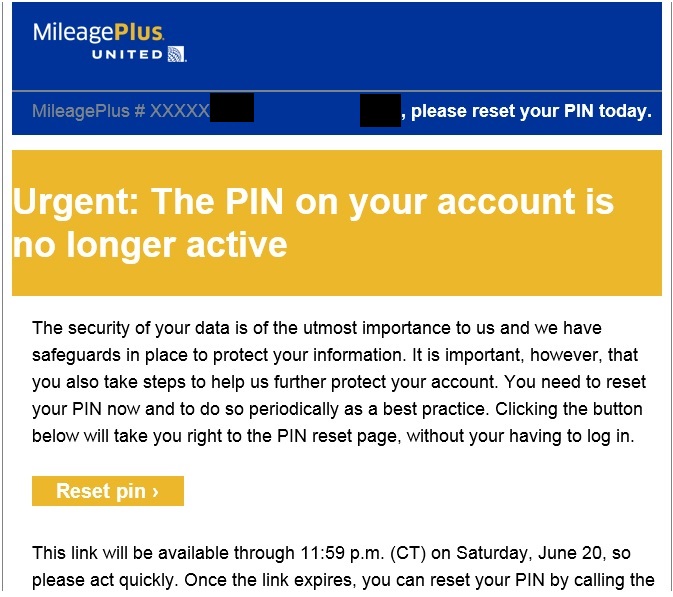
The reset pin link in the email, while convenient as a direct link to the password change page without any other request to authenticate, hardly seems like one of those. I guess it’s ok for United members to click on those links as long as the email actually comes from United, and isn’t an email made to look like it’s come from United, right?
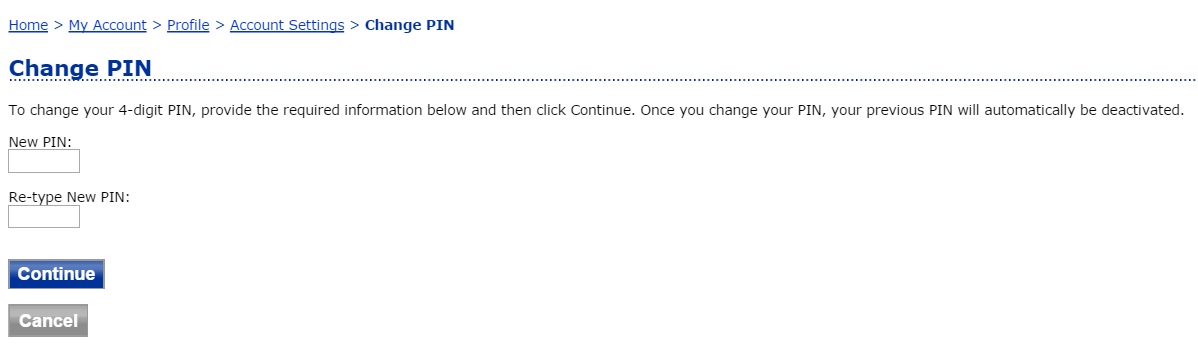
The fact that they don’t ask for your current pin helps give you confidence it’s real, they only want a new pin. That’s enough to be comforting here, right?
And do you think that forwarding United their own email would be good for a million miles?
(HT: Joel G.)


It’s not just United. My SO tried to reset her password on an old Virgin Altantic account last week and instead of sending a password reset link it just emailed her the password, in plain text! Combine that with the ludicrously simple and restrictive password rules and you’ve got a recipe for disaster (simple passwords, not even hashed let alone salted that are emailed in plain text).
Don’t tout stuff as if you know it. Lastpass passwords weren’t compromised. Only the masterpass which was encrypted/hashed/salted was of importance and changing that was the only thing needed on the user end. Hackers aren’t phishers, crackers aren’t hackers or phishers…Stop fuzzing all the terms together.
@passwords Lastpass didn’t have the website passwords they stored for users compromised, and I didn’t say that they did.